OBIEE security is defined through using a role-based totally access manage version. It is defined in terms of roles which are aligned to one of a kind listing server groups and customers. In this chapter, we are able to be discussing the additives described to compose a security coverage.
- One can outline a Security shape with the subsequent components
- The directory Server User and Group managed by using the Authentication issuer.
The application roles controlled by means of the Policy shop provide Security coverage with the following additives: Presentation catalog, repository, policy store.
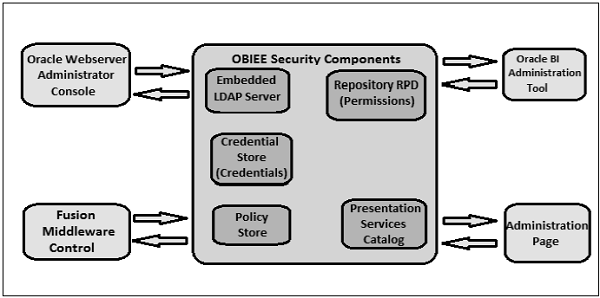
Security Providers
Security company is called in order to get the safety information. Following varieties of security providers are used by OBIEE −
- Authentication company to authenticate customers.
- Policy save company is used to give privileges on all packages besides for BI Presentation Services.
- Credential keep company is used to keep credentials used internally by way of the BI software.
Security Policy
Security policy in OBIEE is split into the subsequent components −
- Presentation Catalog
- Repository
- Policy Store
Presentation Catalog
It defines the catalog items and Oracle BI Presentation Services capability.
Oracle BI Presentation Services Administration
It enables you to set privileges for customers to get admission to functions and features such as modifying perspectives and developing marketers and prompts.
Presentation Catalog privileges get entry to to presentation catalog gadgets described in the Permission dialog.
Presentation Services administration does not have its own authentication gadget and it is based at the authentication machine that it inherits from the Oracle BI Server. All customers who check in to Presentation Services are granted the Authenticated User position and any other roles that they were assigned in Fusion Middleware Control.
You can assign permissions in one of the following methods −
To application roles − Most advocated way of assigning permissions and privileges.
To character customers − This is tough to control wherein you can assign permissions and privileges to particular customers.
To Catalog groups − It turned into used in previous releases for backward compatibility renovation.
Repository
This defines which application roles and users have get admission to to which items of metadata in the repository. The Oracle BI Administration Tool through the security manager is used and permits you to perform the following duties −
- Set permissions for enterprise models, tables, columns, and problem areas.
- Specify database get right of entry to for every user.
- Specify filters to restriction the information handy by means of users.
- Set authentication options.
Policy Store
It defines BI Server, BI Publisher, and Real Time Decisions functionality that can be accessed by given customers or users with given Application Roles.
Authentication and Authorization
Authentication
Authenticator Provider in Oracle WebLogic Server domain is used for person authentication. This authentication issuer accesses users and institution data saved inside the LDAP server in the Oracle Business Intelligence's Oracle WebLogic Server area.
To create and manage customers and corporations in an LDAP server, Oracle WebLogic Server Administration Console is used. You can also pick to configure an authentication company for an opportunity listing. In this example, Oracle WebLogic Server Administration Console enables you to view the users and groups in your directory; however, you want to continue to apply an appropriate tools to make any changes to the listing.
Example − If you reconfigure Oracle Business Intelligence to apply OID, you may view customers and corporations in Oracle WebLogic Server Administration Console but you need to control them in OID Console.
Authorization
Once authentication is completed, the subsequent step in safety is to ensure that the consumer can do and see what they may be legal to do. Authorization for Oracle Business Intelligence 11g is controlled by means of a protection policy in terms of Applications Roles.
Application Roles
Security is typically defined in phrases of Application roles that are assigned to listing server users and companies. Example: the default Application roles are BIAdministrator, BIConsumer, and BIAuthor.
Application roles are defined as practical function assigned to a consumer, which offers that consumer the privileges required to carry out that role. Example: Marketing Analyst Application position would possibly provide a consumer get entry to to view, edit and create reviews on a enterprise's advertising pipeline.
This conversation among Application roles and listing server users and groups allows the administrator to outline the Application roles and regulations without growing additional customers or groups in LDAP server. Application roles allows commercial enterprise intelligence system to be without problems moved between improvement, take a look at and production environments.
This doesn’t require any change in security policy and all that is required is to assign the Application roles to the customers and organizations to be had in the goal environment.
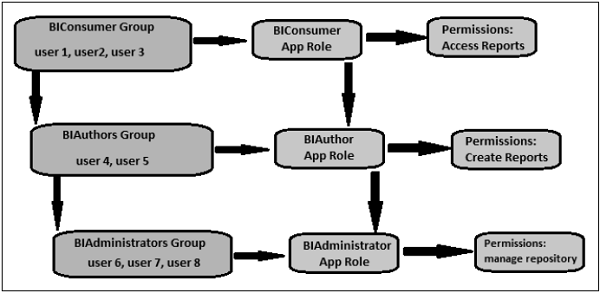
The institution named 'BIConsumers' contains user1, user2, and user3. Users inside the organization 'BIConsumers' are assigned the Application role 'BIConsumer', which allows the users to view reviews.
The group named 'BIAuthors' contains user4 and user5. Users within the organization 'BIAuthors' are assigned the Application function 'BIAuthor', which enables the customers to create reviews.
The group named 'BIAdministrators' contains user6 and user7, user 8. Users in the institution 'BIAdministrators' are assigned the Application role 'BIAdministrator', which enables the users to control repositories.









